software lead weekly
good practise There are several common things and These all take practice. 1. Organization skills/project management skills: ability to pull together internal/external resources, ability to create clear plans, ability to build relationships with other teams to make cross-team collaboration easier 2. Communication skills: ability to deescalate and mediate conflicts fairly, ability to give both positive and negative feedback regularly, ability to create psychological safety, ability to deliver bad news while maintaining psychological safety, ability to run efficient meetings, ability to make unpopular decisions while still commanding the team’s respect, ability to engage with different personality types and communication styles 3.
Kernel Bypass Networking
RDMA (Remote Direct Memory Access), TOE (TCP Offload Engine), and OpenOnload. More recently, DPDK (Data Plane Development Kit) has been used in some applications to bypass the kernel, and then there are new emerging initiatives such as FD.io (Fast Data Input Output) based on VPP (Vector Packet Processing). More will likely emerge in the future.
Technologies like RDMA and TOE create a parallel stack in the kernel and solve the first problem (namely, the “kernel is too slow”) while OpenOnload, DPDK and FD.
Aws Dynamodb Notes
QUERY
aws dynamodb scan --table-name "orders"

公有云羊毛党使用秘籍(新手篇)
本文所说的新手是指还在12个月免费期内的用户
只要有一张信用卡,就可以注册一个AWS账号。
对于AWS新注册账号,有12个月的免费使用额度
具体额度如下:
服务
服务 额度 当月使用统计 服务器 750小时 t2.micro 硬盘 30GB 硬盘快照 1GB 网盘 5G 数据库 25G 函数计算 1百万次调用 下图我这个月的使用额度
计算和存储 从上面的图可以看出,AWS免费额度里面比较鸡肋的是
网盘快照的额度太少,走常规的操作系统镜像备份是要
花钱的,因为一个最小的ubuntu实例镜像就是8G,
如何做到保存自己的最新工作成果,而又额外使用快照从而
节省存储费用呢?
解决办法如下:
硬盘外挂 创建EC2
创建一块硬盘,小于20G即可,并把该硬盘外挂到EC2
在外挂的硬盘里面保存自己的操作数据
使用user_data初始化包括安装常用软件包,自动外挂硬盘等
使用完EC2销毁即可(卸载外挂硬盘千万不要销毁外挂的硬盘)
上面的操作可以使用基础设施配置工具(ansible, terraform, pupport等)
Graph Processing
twitter social network dataset
http://law.di.unimi.it/datasets.php
A comparison of state-of-the-art graph processing systems
Linkedin graph database
https://engineering.linkedin.com/teams/data/projects/search-and-discovery https://engineering.linkedin.com/teams/data
Why I left Apache Spark GraphX and returned to HBase for my graph database
6 Principles of Software Design
1. Single Responsibility Principle Definition: The single responsibility principle is also known as the single-function principle, that is, there is no more than one reason for the class change. In layman’s terms, a class is only responsible for one responsibility. Principle: If a class has too many responsibilities, it is equivalent to coupling these responsibilities together. A change in responsibilities may weaken or continue the ability of this class to perform other duties.
Ubuntu Vpn Client
安装客户端 sudo apt-get install m2crypto pip install shadowsocks /etc/shadowsocks.json
{ "server":"4.1.33.104", "server_port":8388, "local_address": "127.0.0.1", "local_port":1080, "password":"", "timeout":600, "method":"aes-256-cfb" } sslocal -c /etc/shadowsocks.json # To run in the background sudo sslocal -c /etc/shadowsocks.json -d start 配置代理 sudo apt-get install polipo /etc/polipo/config
logSyslog = true logFile = /var/log/polipo/polipo.log logSyslog = true logFile = /var/log/polipo/polipo.log proxyAddress = "0.0.0.0" socksParentProxy = "127.0.0.1:1080" socksProxyType = socks5 chunkHighMark = 50331648 objectHighMark = 16384 serverMaxSlots = 64 serverSlots = 16 serverSlots1 = 32 sudo service polipo stop sudo service polipo start export http_proxy=http://127.
Gitlab Notes
push to a mirror repository push to github at same time when a commit is pushed to gitlab
Protected Branches By default, protected branches are designed to:
prevent their creation, if not already created, from everybody except Maintainers prevent pushes from everybody except Maintainers prevent anyone from force pushing to the branch prevent anyone from deleting the branch Project members permissions NOTE:
In GitLab 11.0, the Master role was renamed to Maintainer The following table depicts the various user permission levels in a project.
Redis With Spring Boot V2
LETTUCE VS JEDIS While Jedis is easy to use and supports a vast number of Redis features, it is not thread safe and needs connection pooling to work in a multi-threaded environment. Connection pooling comes at the cost of a physical connection per Jedis instance which increases the number of Redis connections.
Lettuce, on the other hand, is built on netty (https://netty.io/) and connection instances can be shared across multiple threads.
K8s日志EFK
namespace kube-logging.yaml
kind: Namespace apiVersion: v1 metadata: name: kube-logging headless service
kubectl create -f kube-logging.yaml elasticsearch_svc.yaml
kind: Service apiVersion: v1 metadata: name: elasticsearch namespace: kube-logging labels: app: elasticsearch spec: selector: app: elasticsearch clusterIP: None ports: - port: 9200 name: rest - port: 9300 name: inter-node PROVISION local PV for EFK local PV
Creating the StatefulSet elasticsearch_statefulset.yaml
apiVersion: apps/v1 kind: StatefulSet metadata: name: es-cluster namespace: kube-logging spec: serviceName: elasticsearch replicas: 1 selector: matchLabels: app: elasticsearch template: metadata: labels: app: elasticsearch spec: containers: - name: elasticsearch image: docker.
Docker Dockerfile ENTRYPOINT
Dockerfile ENTRYPOINT有两种形式
exec shell exec(preferred) shell ENTRYPOINT [“executable”, “param1”, “param2”] command param1 param2 Command line arguments to docker run appended not being used ENTRYPOINT will be started as a subcommand of /bin/sh -c default N/A /bin/sh -c (start it with exec to sned stop signal) CMD [“exec_cmd”, “p1_cmd”] exec_entry p1_entry exec_cmd p1_cmd /bin/sh -c exec_entry p1_entry ENTRYPOINT exec FROM alpine:3.
购买笔记本电脑的正确打开姿势
关闭网络连接
个性化设置
性能模式
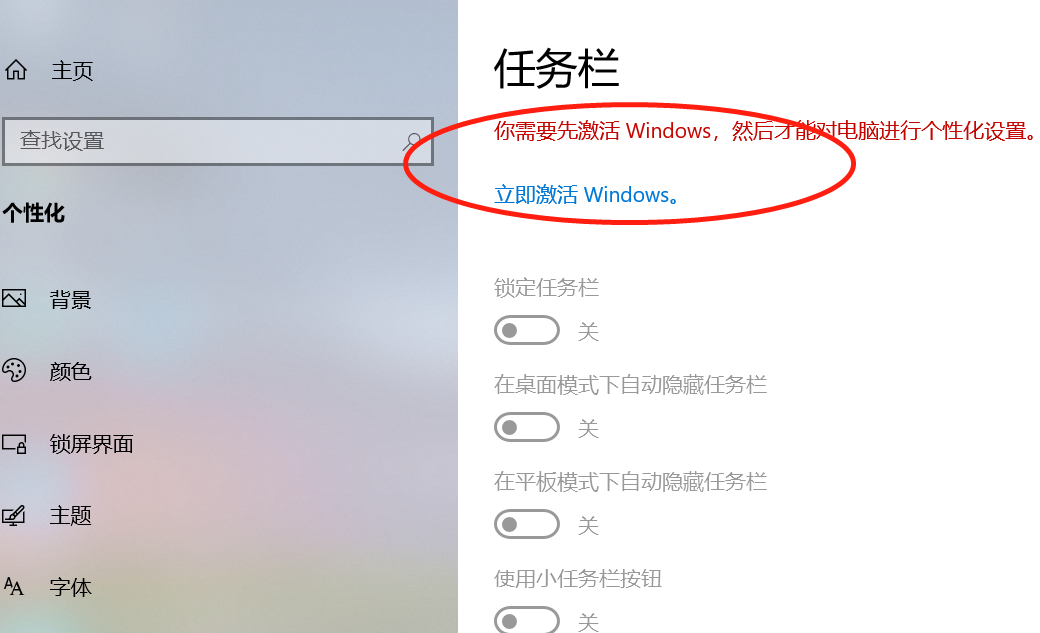
任务栏
通知
文件夹
关闭激活服务
禁用激活服务
https://www.wikihow.com/Turn-Off-Windows-Activation
关闭自动激活
https://www.intowindows.com/how-to-turn-off-automatic-activation-in-windows-10/
注意
个性化设置必须在关闭激活服务之前完成
禁止用户修改密码
net users
net user user_cmp /PasswordChg:No
关闭后台服务
turn off the background app functionality
Start > Settings > Privacy > Background apps
openstack notes
multiple neutron nodes with only one node attached to external network In a typical OpenStack deployment you do not bind Nova instances directly to the external network. As you have already surmised, this won’t work because that network isn’t provisioned on the compute hosts.
Instead, you attach your instances to an internal network, and then you assign floating ip addresses from the external network using,e.g., nova floating-ip-create and nova floating-ip-associate.
streaming note
log-based vs memory-based broker “Thus, in situations where messages may be expensive to process and you want to parallelize processing on a message-by-message basis, and where message ordering is not so important, the JMS/AMQP style of message broker is preferable. On the other hand, in situations with high message throughput, where each message is fast to process and where message ordering is important, the log-based approach works very well.”
UAA Shiro Notes
RequiresUser annotation Requires the current Subject to be an application user for the annotated class/instance/method to be accessed or invoked. This is less restrictive than the RequiresAuthentication annotation.
Shiro defines a “user” as a Subject that is either “remembered” or authenticated:
An authenticated user is a Subject that has successfully logged in (proven their identity) during their current session. A remembered user is any Subject that has proven their identity at least once, although not necessarily during their current session, and asked the system to remember them.
Backends for Frontends
Backends for Frontends
Docker Check Config
#!/usr/bin/env bash set -e EXITCODE=0 # bits of this were adapted from lxc-checkconfig # see also https://github.com/lxc/lxc/blob/lxc-1.0.2/src/lxc/lxc-checkconfig.in possibleConfigs=( '/proc/config.gz' "/boot/config-$(uname -r)" "/usr/src/linux-$(uname -r)/.config" '/usr/src/linux/.config' ) if [ $# -gt 0 ]; then CONFIG="$1" else : ${CONFIG:="${possibleConfigs[0]}"} fi if ! command -v zgrep &> /dev/null; then zgrep() { zcat "$2" | grep "$1" } fi kernelVersion="$(uname -r)" kernelMajor="${kernelVersion%%.*}" kernelMinor="${kernelVersion#$kernelMajor.}" kernelMinor="${kernelMinor%%.*}" is_set() { zgrep "CONFIG_$1=[y|m]" "$CONFIG" > /dev/null } is_set_in_kernel() { zgrep "CONFIG_$1=y" "$CONFIG" > /dev/null } is_set_as_module() { zgrep "CONFIG_$1=m" "$CONFIG" > /dev/null } color() { local codes=() if [ "$1" = 'bold' ]; then codes=( "${codes[@]}" '1' ) shift fi if [ "$#" -gt 0 ]; then local code= case "$1" in # see https://en.

K8S网络基础
K8S网络基础
K8S简介
K8S是自动化部署和监控容器的容器编排和管理工具。各大云厂商和应用开发平台都提供基于K8S的容器服务。 如果觉得K8S托管服务不容易上手或者和本公司的业务场景不很匹配,现在也有很多工具帮助在自己的数据 中心或私有云平台搭建K8S运行环境。
- Minikube
- kops
- kubeadm
如果你想搭建一个测试环境,请参考
Kubernetes主要构件:
- 主节点: 主要的功能包括管理工作节点集群,服务部署,服务发现,工作调度,负载均衡等。
- 工作节点: 应用负载执行单元。
- 服务规范: 无状态服务,有状态服务,守护进程服务,定时任务等。
K8S网络基础
K8S网络模型
- 每一个POD拥有独立的IP地址
- 任何两个POD之间都可以互相通信且不通过NAT
- 集群每个节点上的代理(KUBELET)可以和该节点上的所有POD通信
K8S网络模型从网络端口分配的角度为容器建立一个干净的,向后兼容的规范,极大的方便和简化应用从虚拟机往容器迁移的流程。
K8S解决的网络问题:
- 容器间通信问题: 由POD和localhost通信解决
- POD间通信问题: 由CNI解决
- POD和服务的通信问题: 由SERVICE解决
- 外部系统和SERVICE的通信问题: 由SERVICE解决
Aws Iam Notes
REMOVE ROLE delete policy before delete role
aws iam list-roles aws iam list-role-policies --role-name api-executor aws iam delete-role-policy --role-name api-executor -policy-name "log-writer" aws iam delete-role --role-name pizza-api-executor ADD ROLE POLICY aws iam put-role-policy \ --role-name pizza-api-executor \ --policy-name PizzaApiDynamoDB \ --policy-document file://./roles/dynamodb.json You need to provide a path to dynamodb.json with the file:// prefix. If you are providing an absolute path, keep in mind that you will have three slashes after file:.
Aws Billing Notes
NAT GATEWAY 数据备份S3 Infrequent Access Tier, All Storage / Month $0.0125 per GB
Archive 50 TB into Amazon S3 If you perform a one-time migration of 50 TB of 16 MB files into Amazon S3 in US East (Ohio), it costs you the following to use DataSync: (50 TB copied into S3 * 1024 GB * $0.0125/GB) + (1 S3 LIST request * $0.005 / 1000) + (50 TB / 16 MB S3 PUT requests * $0.